Stored cross-site scripting vulnerability in "Additional TCA" extension for TYPO3 allows attackers to run arbitrary JavaScript code in the browser of other users
Open Source
NTCF:
NTCF-2025-1294
CVE:
CVE-2025-30083
Product:
additional-tca
Vendor:
coding.ms
Criticality:
medium
Status:
fixed
Discovered:
2025-02-06
Detail:
Public
Vulnerable version:
1.7.0 - 1.15.16, 1.16.0 - 1.16.8
Fixed version:
1.15.17, 1.16.9
Summary
"Additional TCA" is an extension for the TYPO3 enterprise Content Management System (CMS). It has been discovered that the versions 1.7.0-1.15.16 and 1.16.0-1.16.8 are susceptible to cross-site scripting (XSS).
The NTC discovered this vulnerability while testing the "Modules" extension from coding.ms, which uses "Additional TCA" as a dependency.
Background
TYPO3 is a widely used open source enterprise CMS known for its extensibility and customizability. It allows organizations to build and manage complex websites while offering a range of extensions that enhance its functionality. Various authorities at the national, cantonal and municipality level use TYPO3 - often in contexts where confidentiality, availability and integrity are essential.
In a pilot project with the NCSC, the NTC evaluated the security of TYPO3 and its extensions to ensure the security of open source software used within the Swiss administration. Read more about the project here.
Vulnerability
The badges feature in "Additional TCA" is vulnerable to XSS.
The snippet below shows part of the code in Classes/Form/Element/BadgeSuggested.php as of f3a126f67cc0207f8b047a7000dc148ece049cfe, which is before the vulnerability was fixed:
if (count($entries) > 0) {
$html[] = '<div class="form-wizards-element-scopes">';
foreach ($entries as $entry)
$html[] = '<a class="' . $badgeClass . '" href="#" style="border-radius: 2px">' . $entry . '</a>' }
$html[] = '</div>';
}The highlighted line reveals that the badge content ($entry) is rendered without encoding.
Proof of Concept
The NTC discovered this vulnerability while testing the "Modules" extension from coding.ms, which uses "Additional TCA" as a dependency.
The XSS can be exploited by creating a frontend user with the following title in the “Website Users” menu in the TYPO3 backend: "><img onerror=alert(1) src=x>.
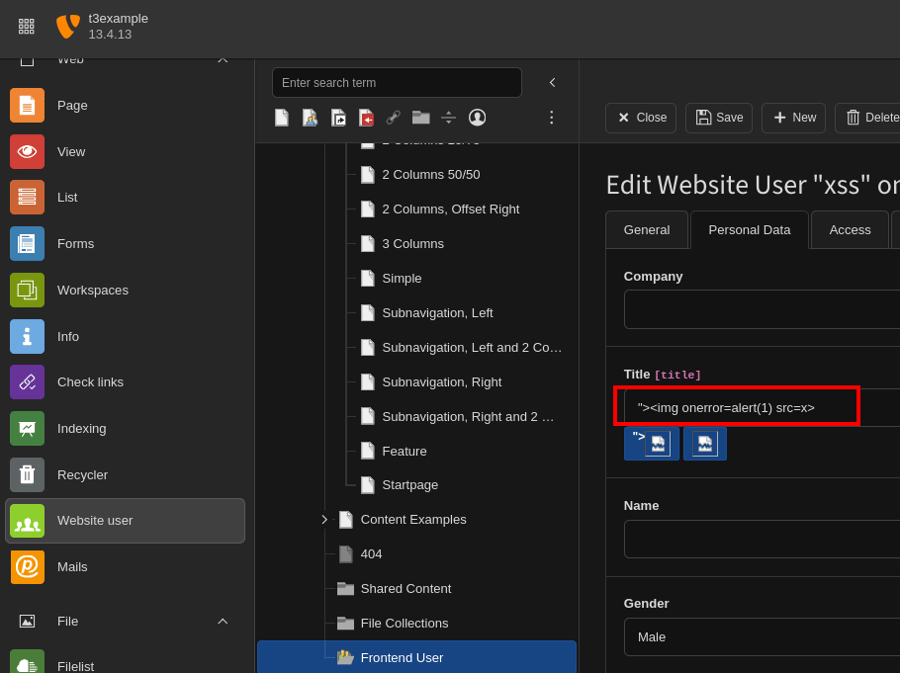
After saving the entry and opening the edit page again, for example by creating a new user, the payload gets executed. This happens because in the "Person Data" tab a badge with the previously entered titles is shown.
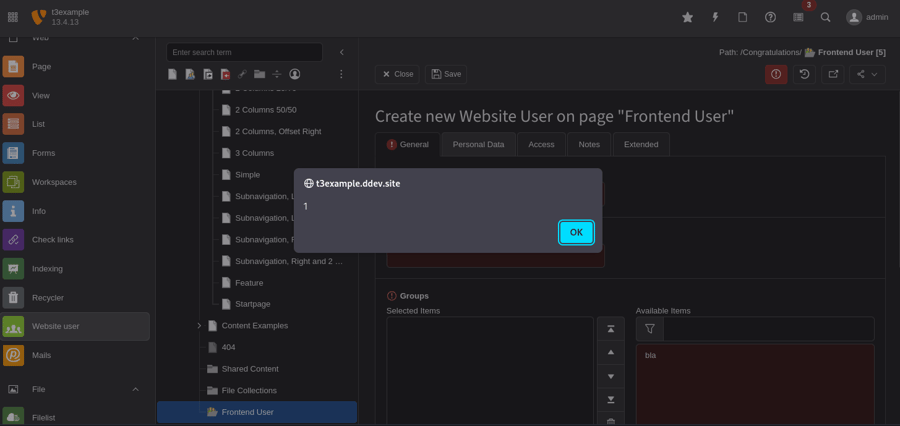
Remediation
This vulnerability was reported to the TYPO3 security team and fixed by the extension maintainers in 348da890d2e2ee914373639af258b098cbda3ba9. This patch introduces encoding within the template.
Patches
This issue has been fixed in version the versions 1.15.17 and 1.16.9. It is recommended that all users of codingms/additional-tca update to the latest version.
Workarounds
Additionally, it is recommended to enable the Content Security Policy (CSP) for the TYPO3 backend user interface, which prevents the execution of this XSS vulnerability.
In TYPO3 13.4, this security feature is enabled by default.
Timeline
2025-02-06: initial discovery
2025-02-21: private disclosure to vendor
2025-03-18: fix by vendor
2025-10-13: public disclosure