Server-side template injection in Peering Manager allows an attacker to execute arbitrary operating system commands (RCE)
Open Source
NTCF:
NTCF-2023-72886
CVE:
CVE-2024-28114
Product:
Peering Manager
Vendor:
Peering Manager
Criticality:
high
Status:
fixed
Discovered:
2023-12-12
Detail:
Public
Vulnerable version:
<=1.8.2
Fixed version:
1.8.3
Summary
Peering Manager is a BGP session management tool. There is a Server Side Template Injection vulnerability that leads to Remote Code Execution in Peering Manager <=1.8.2. As a result arbitrary commands can be executed on the operating system that is running Peering Manager.
Background
Peering Manager is an open-source BGP session management solution built with Python and the Django framework. Designed with features and simplicity in mind, it allows engineers to track, maintain and configure BGP sessions from a centralised management point without the usual tedious manual provisioning task.
The NTC observed that Peering Manager is used by various Swiss internet service providers and started testing it as part of our mission to improve cyber security for the Swiss society.
from django.conf import settings
from jinja2 import Environment, TemplateSyntaxErrorenvironment = Environment(
loader=PeeringManagerLoader(), trim_blocks=trim, lstrip_blocks=lstrip
)
[...]
# Try rendering the template, return a message about syntax issues if there
# are any
try:
jinja2_template = environment.from_string(template)
return jinja2_template.render(**context)Notice that before v1.8.3, the code of templates was directly loaded into the runtime environment of the application and rendered.
There are multiple ways to inject code into Jinja templates that lead to remote code execution. The chapter below shows a method that worked in Peering Manager.
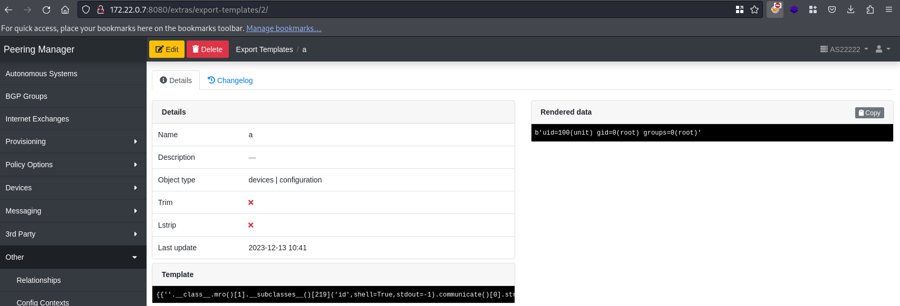
Proof of Concept
- Open
http://[ip]:[port]/extras/export-templates/add/as a user who has access to it. -
Create a template with the following payload, where the subclass
219is theSubprocess.Popencall:
{{''.__class__.mro()[1].__subclasses__()[219]('id',shell=True,stdout=-1).communicate()[0].strip()}}- Fill in the rest of the form and submit it.
- The result of the OS command is shown on the right hand side, confirming the remote code execution.
Remediation
The environment of the templates was sandboxed in commit 8a865fb596c11ad7caf45aef317d8fcbce7f85ff. This should not been seen as a 100% secure solution, but rather a security improvement that keeps the feature usable for its intended purpose.
The documentation now warns users about the potential dangers of the templates.
Patches
This issue has been addressed in version 1.8.3. It is recommended that all users of Peering Manager update to the latest version.
Workarounds
Using a web application firewall in front of the Peering Manager can detect known template injection payloads and preventing them from reaching the vulnerable application.
Operators are still advised to update to the latest version of Peering Manager and ensure all templates added are safe to run.
Timeline
2023-12-12: initial discovery
2023-12-18: first contact to vendor
2024-01-23: private disclosure to vendor
2024-01-23: confirmation by the maintainer and suggestion for a fix
2024-01-25: fix by vendor
2024-01-26: testing and approval of fix by NTC
2024-02-03: version 1.8.3 released containing the fix
2024-03-12: CVE and adviory published by vendor
2024-06-25: public disclosure