Stored Cross-site scripting vulnerability of Peering Manager allows an attacker to execute arbitrary JavaScript code with the permissions of other users
Open Source
NTCF:
NTCF-2023-45061
CVE:
CVE-2024-28112
Product:
Peering Manager
Vendor:
Peering Manager
Criticality:
medium
Status:
fixed
Discovered:
2023-12-12
Detail:
Public
Vulnerable version:
<=1.8.2
Fixed version:
1.8.3
Summary
Peering Manager is a BGP session management tool. Versions <=1.8.2 of Peering Manager are vulnerable to a stored Cross-Site Scripting (XSS) attack in the name attribute of AS or Platform. This allows adversaries to execute arbitrary JavaScript code with the permission of a victim.
Background
Peering Manager is an open-source BGP session management solution built with Python and the Django framework. Designed with features and simplicity in mind, it allows engineers to track, maintain and configure BGP sessions from a centralised management point without the usual tedious manual provisioning task.
The NTC discovered that Peering Manager is used by various Swiss internet service providers and started testing it as part of our mission to improve cyber security for the Swiss society.
Vulnerability
The page source of the router uses a custom as_link filter (From https://github.com/peering-manager/peering-manager/blob/ed5f46a20c9594339d21a9a126e33797227efb8f/templates/peering/router/view.html#L42):
<tr>
<td>Local AS</td>
<td>{{ instance.local_autonomous_system|as_link }}</td>
</tr>utils/templatetags/helpers.py. Before version 1.3.8 the filter was implemented like this:@register.filter()
def as_link(value):
if not hasattr(value, "get_absolute_url"):
return value return mark_safe(f'<a href="{value.get_absolute_url()}">{value}</a>')The highlighted row shows that the provided value does not get escaped and gets marked as safe, which disables Django's built-in auto-escaping mechanism.
The proof of concept below describes ways this oversight could be used to get XSS within Peering Manager.
Proof of Concept
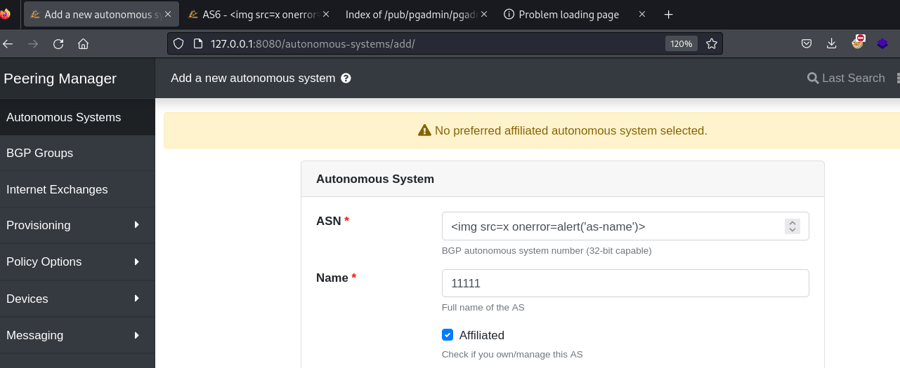
- Create a local autonomous system (
http://[ip]:[port]/autonomous-systems/add/) with the name of an XSS payload like<img src=x onerror=alert('as-name')>and make sure theAffiliatedCheckbox is checked.
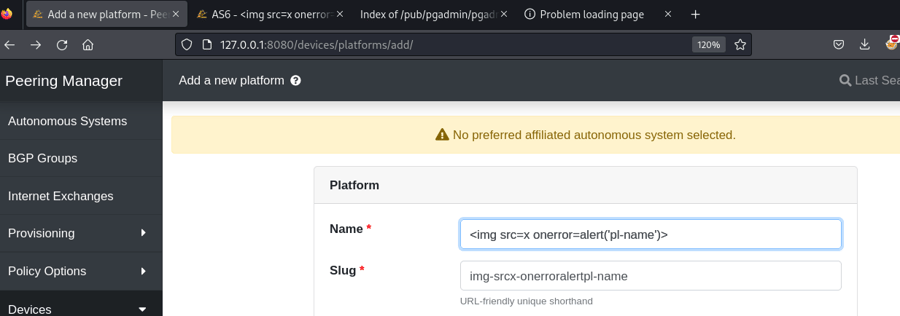
- Create a platform (
http://[ip]:[port]/devices/platforms/add/) with the name<img src="x" onerror="alert('pl-name')">.
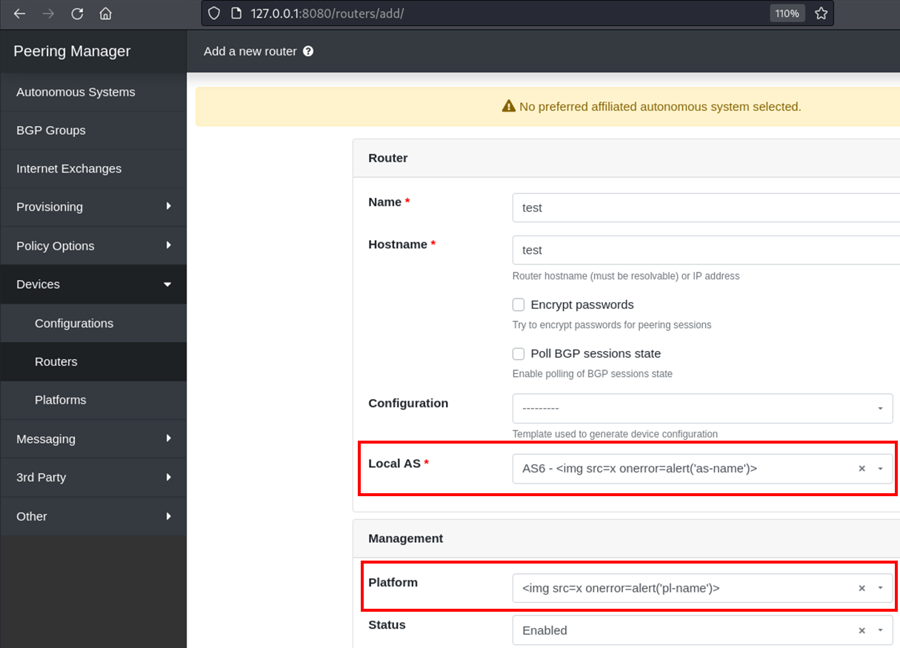
- Create a router (
http://[ip]:[port]/routers/add/) and select the newly created autonomous system and platform in their respective dropdowns.
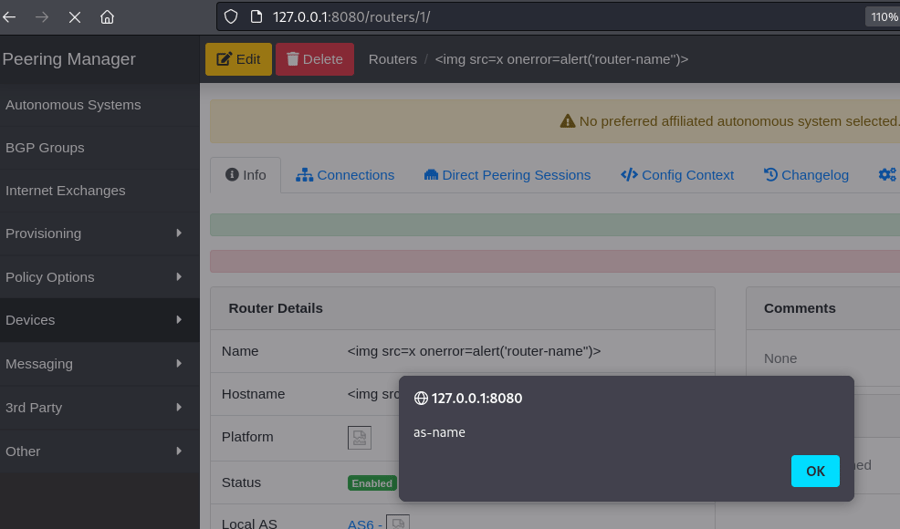
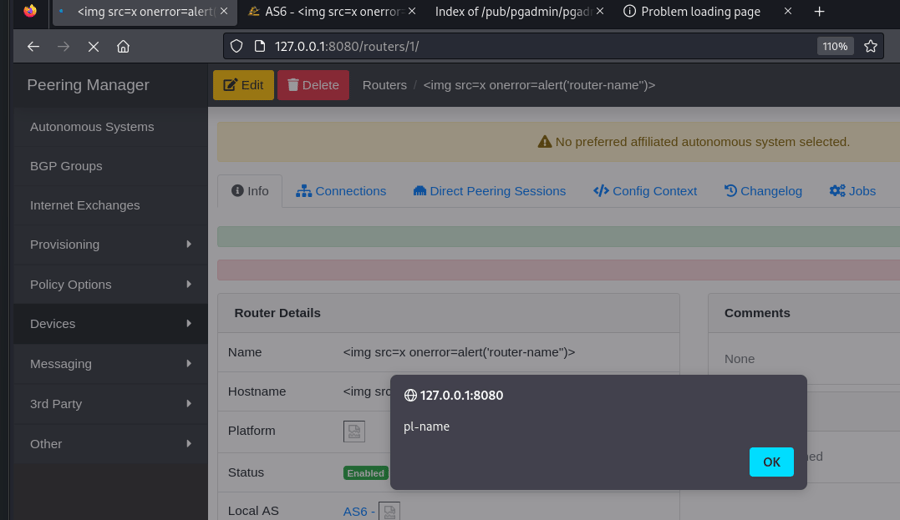
- Open the router’s page that was created:
http://[ip]:[port]/routers/1/and two alert messages will pop up as confirmation for the XSS vulnerability.
Remediation
The vulnerable filter was changed to use the escape mechanism supplied by Django in ad0e69d01fbe3d1e48f951eca4a8ec97194797fa.
Patches
This issue has been fixed in version 1.8.3. It is recommended that all users of Peering Manager update to the latest version. There are no known workarounds for this vulnerability.
Timeline
2023-12-12: initial discovery
2023-12-18: first contact to vendor
2024-01-23: private disclosure to vendor
2024-01-23: confirmation by the maintainer and suggestion for a fix
2024-01-25: fix by vendor
2024-01-26: testing and approval of fix by NTC
2024-02-03: version 1.8.3 released containing the fix
2024-03-12: CVE and adviory published by vendor
2024-06-25: public disclosure